Learn Cloud Networking in 7 minutes
Breaking down the heavy words from VPC, Subnet, Availability Zones, Regions to Security Group in the simplest way on the Internet
Hello Everyone
Welcome to your AKVAverse, I’m Abhishek Veeramalla, aka the AKVAman, your guide for Cloud, DevOps, and AI.
Today we will be talking about the most underrated, but many people lack in this concept. Every Cloud and DevOps engineer should be aware of these terms before appearing for any interview. Yes, I am talking about Cloud Networking, which works as a fundamental prerequisite before jumping to any interview, or even when you are a newbie to Cloud.
In this Newsletter we will be covering VPC, Subnet, Availability Zones, Regions and also the most important Security Groups. After reading this Newsletter you will be an expert in explaining these topics in any interview.
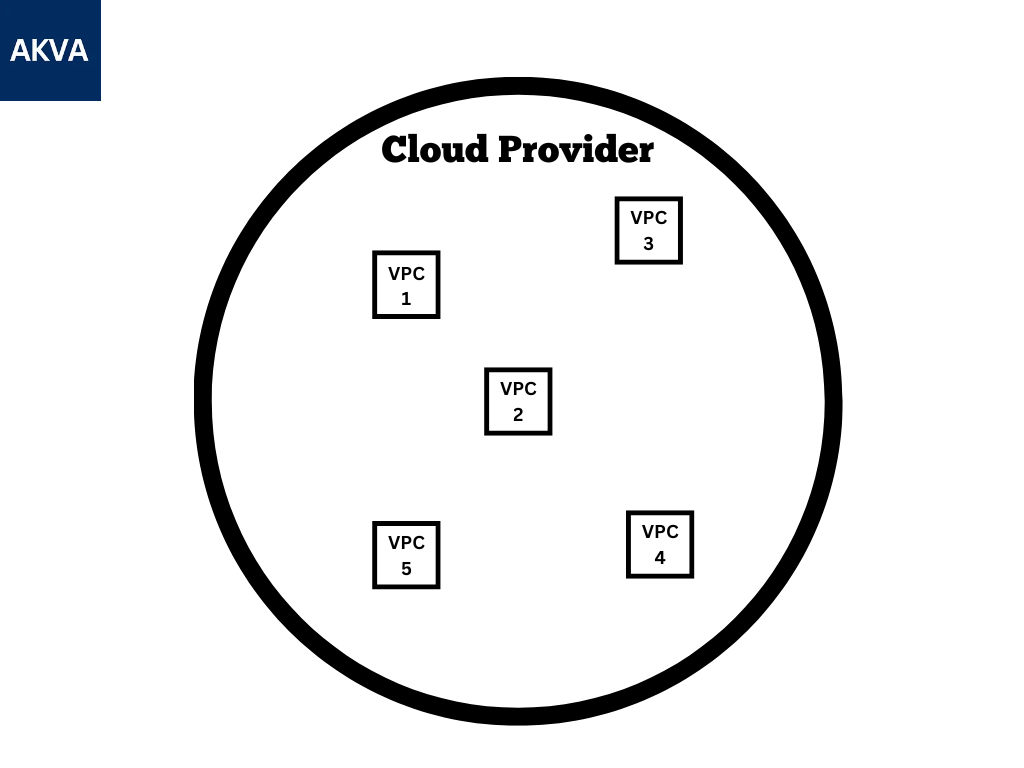
VPC (Virtual Private Cloud)
Think of VPC as your personal cloud where you host your Infrastructure. It is a logically separated system for your Infrastructure. VPC help you to host your infrastructure on a range of IP addresses. Now you would think how we are going to separate it from others this is the same question I thought when I heard this term first time, and the answer to it is the CIDR Range (Classless Inter-Domain Routing). So CIDR is what it helps us to isolate our Infra from others. CIDR Block will look something like this 10.0.0.0/16. Comment down how many IPs will be assigned to this CIDR, along with the calculation you had done.
VPC is similar to owning a Row House in a Gated Society, where you have your land, your house, you don't need to worry about how it will get built who will be taking care of labour and all, you just come with your family and live there happily. Similarly, in VPC, you come and host our infrastructure inside it, we don’t worry about who will take care of the network and the infrastructure where it is hosted.
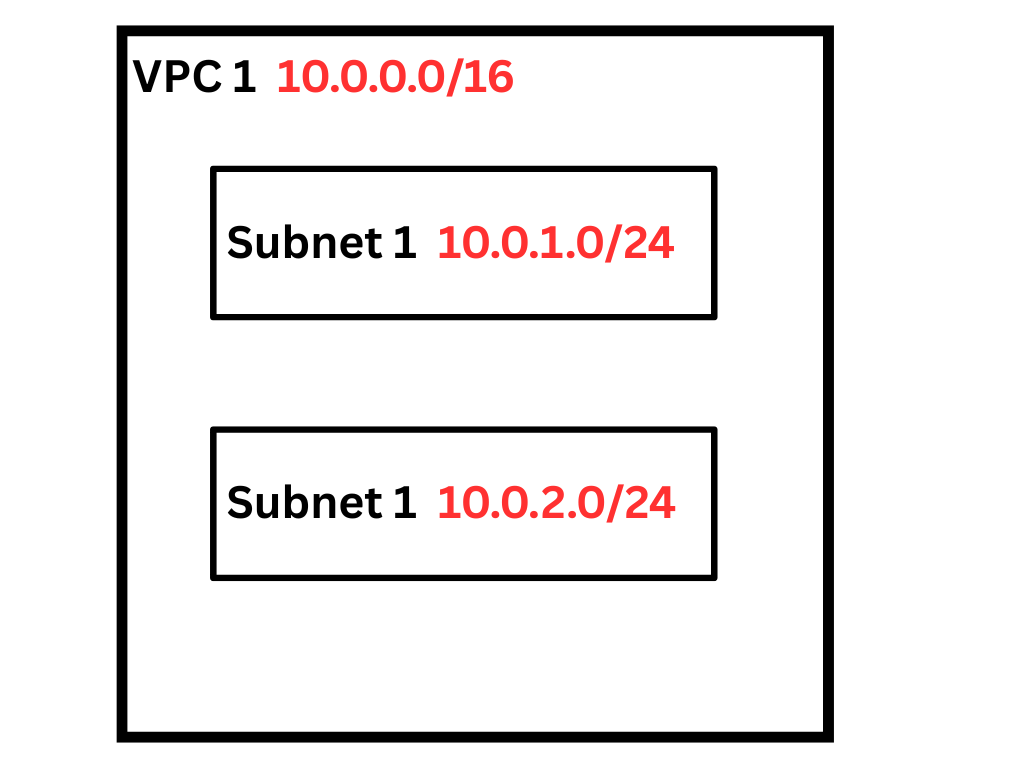
Subnet
If VPC is your Row house, then subnets are the rooms inside your house where you divide the entire VPC into small and manageable sections, where you peacefully place your different parts of infrastructure.
For your interview, you can say that it is a logical separation of a larger group of IP ranges into smaller groups.
When you create a VPC, the Subnet lies inside your CIDR Range.
Let discuss it with an example
Suppose you have a CIDR range of 10.0.0.0/16 then your Subnet will be 10.0.1.0/24, 10.0.2.0/24
We also have 2 types of subnets, the public and private subnet.
Public Subnet: Public subnet connects to the Internet Gateway, and in this subnet we host our WebServers, Loadbalancer that are internet-facing.
Private Subnet: In this Subnet, there is no direct rule to connect to the internet, and in this subnet, we host our Databases, backend services, or internal apps.
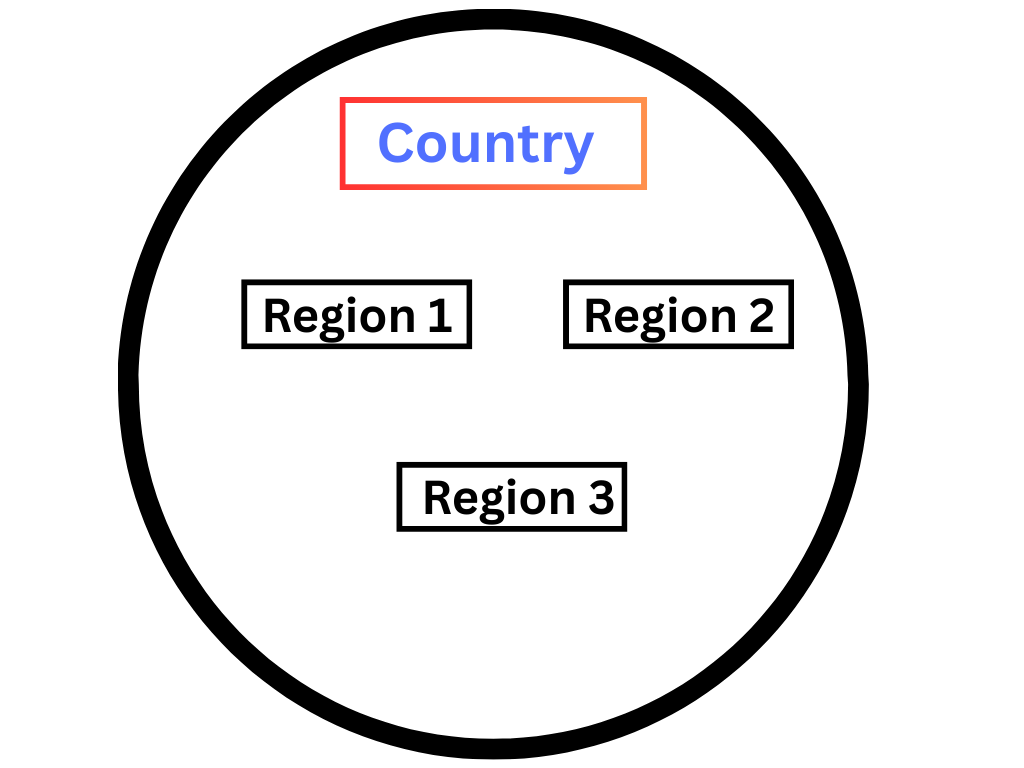
Regions
We talked about VPC and Subnet but till now do you even think, okay, Abhishek we understand the Row house and the rooms inside it but can you expalin where the Row house is, and this is the reason I will be talking about the Regions, A Region is a specific geographical area where your cloud provider (AWS, Azure, GCP) hosts their server. These Regions are independent of each other. Each region is divided into different Availability Zones on which we will be talking about in the next part.
Do you think why we need regions? The sole reason for having regions is the latency and different government policies that stop the cloud providers from storing the data outside the country.
Consider the Regions as different cities in a country. Comment down the Regions that AWS have in India.
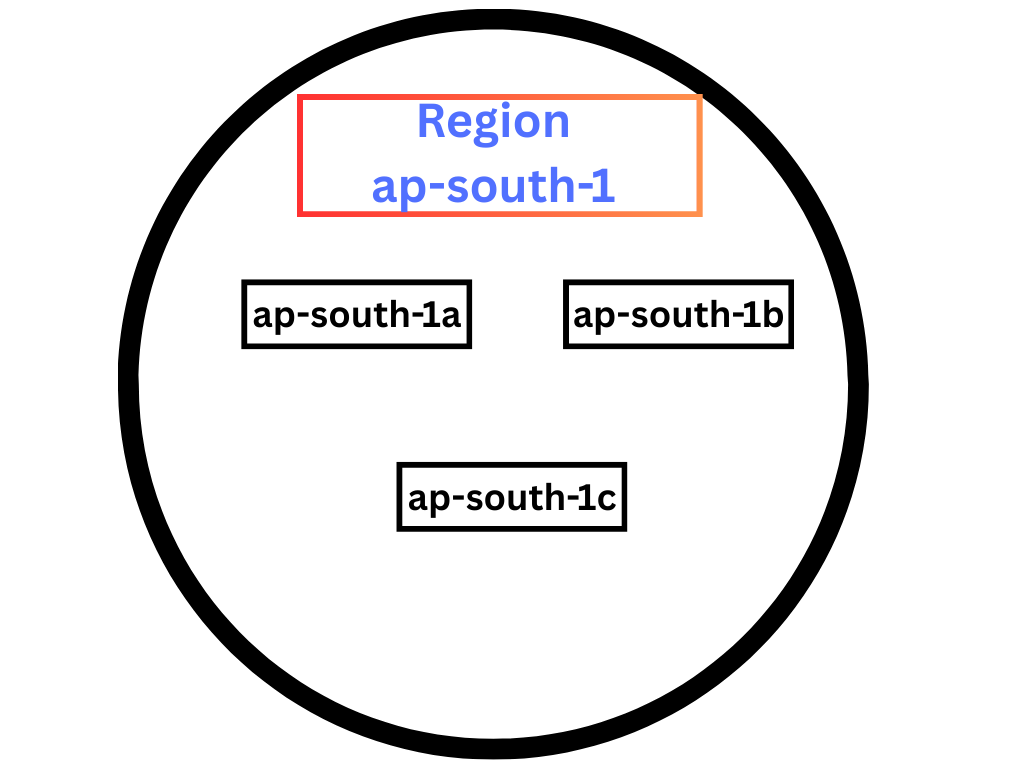
Availability Zones
The Availability Zones lie inside a Region, and we have multiple AZs inside a Region but not multiple Regions inside AZs. The Regions are like the city, and the AZ is like the different areas inside a city which are independent from other Availability Zones in terms of power, cooling, and networking, but they are connected with super ultra low latency links.
This means they are independent enough to run alone in the situation of failure or natural calamity and connected enough to trsnsfer data in a second.
The reason for having multiple AZs inside a region is that it promises us to run our application even if one of the data centers goes down, think like you put all your belongings in a single hous,e and if that house catches fire or gets robbed you will lose everything, but when we spread across multiple house we will have something in our hands.
Security Group
Security Group is like the security guard which sit outside of your society for your Row house, they handle who will go in and who will go out of the society. Similarly, a Security group handles the traffic for each of your resources inside the cloud; they are like a virtual firewall attached to your every resource from EC2 to Database to Load Balancer.
Security groups are default deny which means they deny everything until you specifically decide what to allow to reach your servers.
There are mainly 2 types of rules that we decide in a security group
Inbound rules: Inbound rules decide the kind of traffic that can reach your servers.
Outbound rules: Outbound rules decide the kind of traffic that can go out (leave) from your servers.
Think of it like your Instagram privacy settings:
We choose who can message us (inbound).
We choose whom we can message (outbound).
A Thought to Leave You With
VPC: Row House
Subnet: Rooms in the house
Regions: City in a country
Availability Zones: Ares inside a City
Security groups: Security guard of your society of your Row House
Hope you love this analogy. Let me know which analogy you love the most.
So start small, stay curious, and get hands-on.
Until next time, keep building, keep experimenting, and keep exploring your AKVAverse. 💙
Abhishek Veeramalla, aka the AKVAman.

Thanks for the knowledge👍
In the doc, below both inbound and outbound analogy are same?
We choose who can message us (inbound).
We choose who can message us (outbound).
The analogy is amazing sir❤️
Thanks for sharing it.